Introduction:
In today’s cloud-first world, data security is paramount. With sensitive information transmitted and stored online, protecting it from unauthorized access is crucial. Amazon Web Services (AWS) Key Management Service (KMS) is a game-changer in cloud security, providing a secure and scalable solution for managing encryption keys. In this article, we’ll delve into the world of AWS KMS, exploring its benefits, features, and best practices to help you safeguard your cloud data.
AWS KMS (Key Management Service):
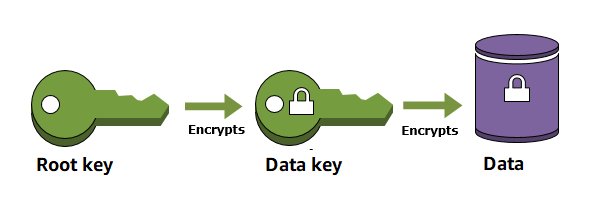
AWS Key Management Service (AWS KMS) is an AWS managed service that makes it easy for you to create and control the encryption keys that are used to encrypt your data. The AWS KMS keys that you create in AWS KMS are protected by FIPS 140-2 validated hardware security modules (HSM). They never leave AWS KMS unencrypted. To use or manage your KMS keys, you interact with AWS KMS
AWS KMS offers two types of managed keys:
1. AWS Managed Keys (Aws/managed)
- Description: These keys are automatically created, managed, and rotated by AWS for use with AWS services. They are designed to make encryption easier by handling key management tasks on your behalf.
- Usage: Ideal for scenarios where you want basic encryption without the need for granular control over the keys. For example, when you enable encryption on an Amazon S3 bucket, EBS volume, or RDS instance, AWS will use an AWS-managed key by default.
- Rotation: AWS automatically rotates these keys every three years.
- Access Control: AWS controls the key policies, so you don’t have direct access to modify them.
2. Customer Managed Keys (CMKs)
- Description: These keys are created and managed by you, providing more control over the encryption process. You can create, manage, enable/disable, and define access control policies for these keys.
- Usage: Suitable when you require more control over key management, such as specifying key rotation policies, managing key permissions, or having keys that work across multiple AWS accounts and regions.
- Rotation: You have the option to enable automatic key rotation every year or rotate keys manually whenever needed.
- Access Control: You can define detailed key policies and IAM policies to control who can use or manage your CMK
Features Of KMS
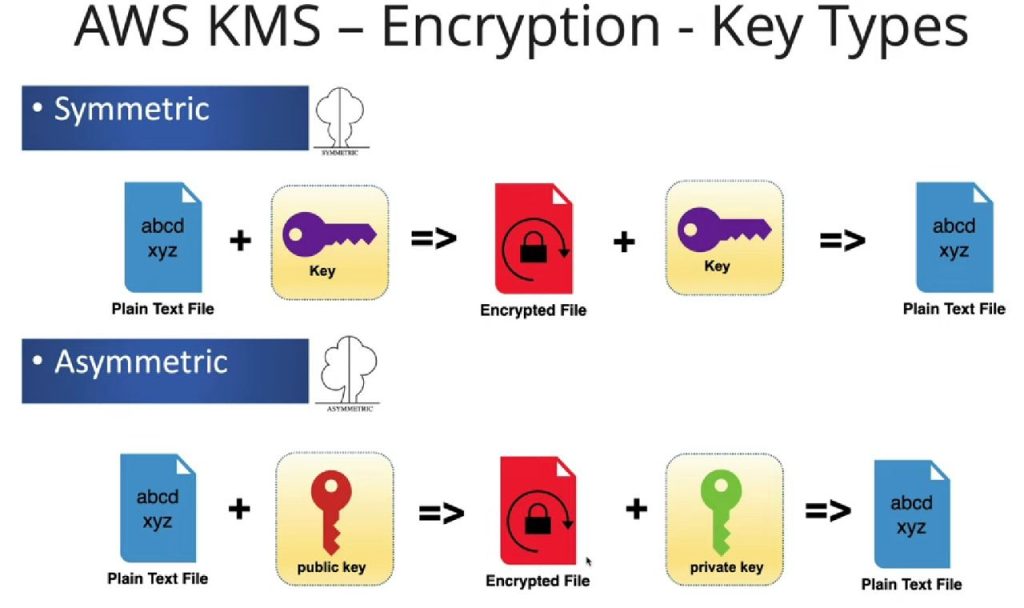
Symmetric and Asymmetric Encryption: AWS KMS supports both symmetric and asymmetric encryption algorithms.
- Symmetric encryption (AES): Same key for encryption and decryption.
- Asymmetric encryption (RSA, ECC): Different keys for encryption and decryption.
Key Policies and Permissions: Control access to encryption keys using customizable key policies.
- Define permissions for key usage.
- Specify allowed actions (e.g., Encrypt, Decrypt).
- Support for AWS IAM policies.
Automatic Key Rotation: Rotate encryption keys automatically.
- Schedule key rotation (e.g., every year).
- New key is generated and old key is retired.
- Seamless key rotation without disrupting applications.
CloudTrail Logging and Monitoring: Monitor AWS KMS API calls using AWS CloudTrail.
- Log key usage and access attempts.
- Track changes to key policies and permissions.
- Integrate with AWS CloudWatch for real-time monitoring.
Integration with AWS IAM: Seamless integration with AWS Identity and Access Management (IAM).
- Use IAM roles to control access to encryption keys.
- Define IAM policies for key usage.
- Support for IAM identity federation.
Custom Key Stores: Create and manage custom key stores.
- Store sensitive keys securely.
- Control access to custom key stores.
- Support for external key storage.
Secure Key Import: Import existing keys securely.
- Support for key wrapping and unwrapping.
- Secure key transfer using AWS KMS APIs.
- Verify key integrity and authenticity.
AWS service integration
AWS KMS integrates with AWS services to encrypt data at rest, or to facilitate signing and verification using an AWS KMS key. To protect data at rest, integrated AWS services use envelope encryption, where a data key is used to encrypt data and is itself encrypted under a KMS key stored in AWS KMS. For signing and verification, integrated AWS services use asymmetric RSA or ECC KMS keys in AWS KMS.
Case Study: Protecting Customer Data with AWS KMS and Amazon S3
Case 1: Securing Personal Health Information in Amazon S3
Scenario:
A healthcare startup, “HealthSecure,” provides an application for storing and analyzing patient health records. As part of its services, HealthSecure stores large amounts of sensitive Personal Health Information (PHI) in Amazon S3. The company must comply with stringent data protection laws like HIPAA, which mandates encryption of sensitive data both at rest and in transit. HealthSecure needed a solution to ensure that the PHI stored in Amazon S3 is securely encrypted and that only authorized healthcare providers and applications could access it. They also needed a simple and scalable way to manage encryption keys without manual overhead.
Solution:
HealthSecure chose AWS KMS to manage encryption keys and Amazon S3 with Server-Side Encryption with AWS KMS-Managed Keys (SSE-KMS) for data encryption at rest. Here’s the setup they implemented:
- Encryption of S3 Objects:
- HealthSecure configured Amazon S3 buckets to use SSE-KMS for all objects. Each health record uploaded to S3 is encrypted using a KMS Customer Managed Key (CMK) before being stored.
- They applied bucket policies to enforce encryption using KMS-managed keys, ensuring that no object is stored in unencrypted form.
- Access Control and Key Management:
- AWS KMS key policies were implemented to strictly control access to encryption keys. Only authorized users and healthcare applications had permission to decrypt the data, while unauthorized users were denied access.
- HealthSecure leveraged IAM roles to allow their application servers and Lambda functions to securely access encrypted data in S3 without exposing the encryption keys.
Data Encryption in Transit:
- HealthSecure ensured that data was encrypted during transmission by enforcing TLS/SSL connections between the healthcare application and Amazon S3.
- Auditing and Compliance:
- AWS CloudTrail was enabled to log all AWS KMS API requests related to encryption and decryption, providing an auditable trail for compliance with HIPAA.
- AWS CloudWatch was set up to monitor and alert on any unauthorized access attempts, ensuring real-time monitoring of potential security breaches.
- By admin





