INTRODUCTION:
Amazon CloudWatch Logs offers a data protection capability, Amazon CloudWatch Logs data protection, that can automatically mask sensitive data when it is logged. When enabled, pattern matching and machine learning (ML) based masks are applied to match and replace sensitive data types like credit card numbers, social security numbers, and others with asterisks (*). Currently there are many pre-built managed data identifiers that can be used out of the box and easily applied at scale. In addition to this, CloudWatch Logs Data Protection offers the capability to define custom data identifiers to fit your business specific needs.
- Data Masking: You can mask sensitive data in log events using data protection policies, which audit and mask sensitive data that matches selected data identifiers
- You can enable a data protection policy for new or existing log groups from the AWS Management Console, From the console, select any log group and create a data protection policy in the Data protection
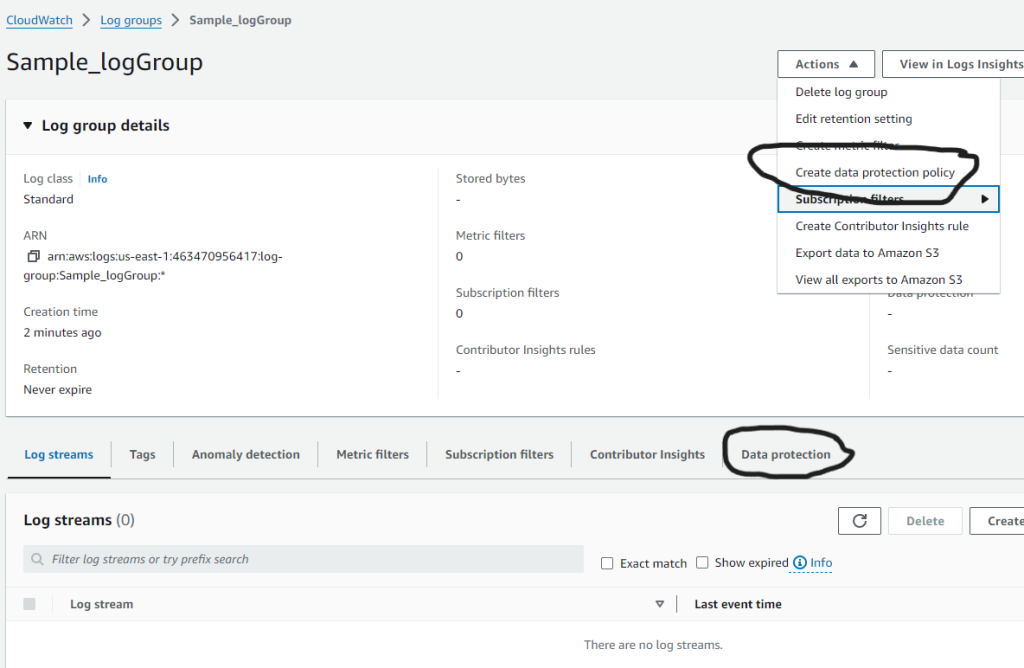
- When you create Data Protection , you can specify the data you want to protect. Choose from over 100 managed data identifiers, which are a repository of common sensitive data patterns spanning financial, health, and personal information. This feature provides you with complete flexibility in choosing from a wide variety of data identifiers that are specific to your use cases or geographical region.
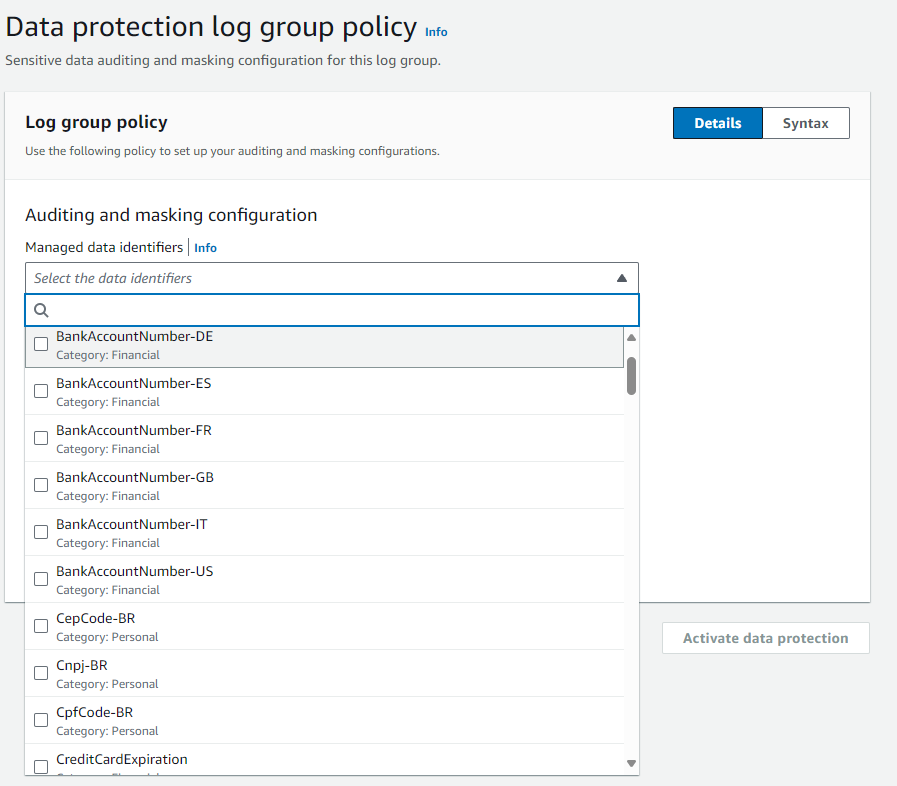
- You can also enable audit reports and send them to another log group, an Amazon Simple Storage Service (Amazon S3) bucket, or Amazon Kinesis Firehose. These reports contain a detailed log of data protection findings.
- If you want to monitor and get notified when sensitive data is detected, you can create an alarm around the metric
LogEventsWithFindings. This metric shows how many findings there are in a particular log group. This allows you to quickly understand which application is logging sensitive data.
Data Protection Features
- Encryption at Rest: CloudWatch Logs protects data at rest using encryption. All log groups are encrypted. By default, the CloudWatch Logs service manages the server-side encryption and uses server-side encryption with 256-bit Advanced Encryption Standard Galois/Counter Mode (AES-GCM) to encrypt log data at rest.
If you want to manage the keys used for encrypting and decrypting your logs, use AWS KMS keys. For more information, see Encrypt log data in CloudWatch Logs using AWS Key Management Service.
- Encryption in Transit: CloudWatch Logs uses end-to-end encryption of data in transit, with server-side encryption keys managed by the service.
- Data Masking: You can mask sensitive data in log events using data protection policies, which audit and mask sensitive data that matches selected data identifiers.
- Access Control: For data protection purposes, recommend that you protect AWS account credentials and set up individual users with AWS Identity and Access Management (IAM). That way, each user is given only the permissions necessary to fulfill their job duties. We also recommend that you secure your data in the following ways
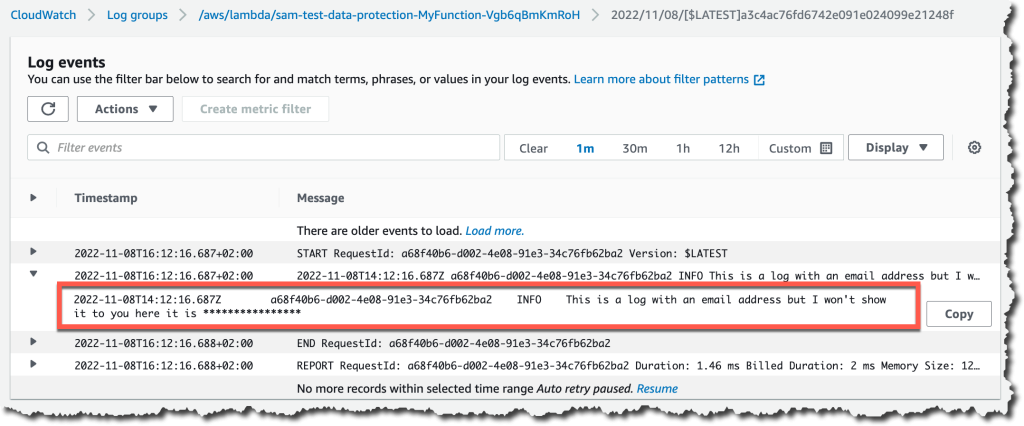
- Only users with elevated privileges in their IAM policy (add
logs:Unmaskaction in the user policy) can view unmasked data in CloudWatch Logs Insights, logs stream search, or via FilterLogEvents and GetLogEvents APIs
- Amazon CloudWatch Logs data protection pricing is based on the amount of data that is scanned for sensitive information. You can check the CloudWatch Logs pricing page to learn more about the pricing of this feature in your Region
- By admin





