In this post, I’ll guide you on how to use Amazon EC2 Instance Connect to securely SSH into your Amazon EC2 instances that are running in private subnets within an Amazon VPC.
This approach is ideal for customers who:
- Need SSH access to EC2 instances in a private subnet.
- Want to stop managing long-term SSH keys.
- Need to restrict SSH session sources.
While EC2 Instance Connect needs access to the public endpoint for some functions, your actual SSH traffic can stay within your private network. This setup offers strong access control and simplifies key management.
Overview of how EC2 Instance Connect works
EC2 Instance Connect uses AWS IAM and temporary SSH keys to manage access.
- An IAM policy attached to an IAM user or role controls access.
- When an authorized user wants to connect, a one-time SSH public key is sent to the EC2 Instance Connect API.
- The SSH client must connect using the matching private key within that time frame
Ways to Connect:
You can use EC2 Instance Connect in three ways:
- Access via the AWS Management Console for instances with public IPs.
- Your Own SSH Client: For instances without public IPs.
- EC2 Instance Connect CLI: For command-line access.
Example Network Setup and IAM Policy
Let’s Imagine your cloud setup is an extension of your on-premises data centre, connected via AWS Direct Connect. You need a scalable way for users to access EC2 instances without managing SSH keys.
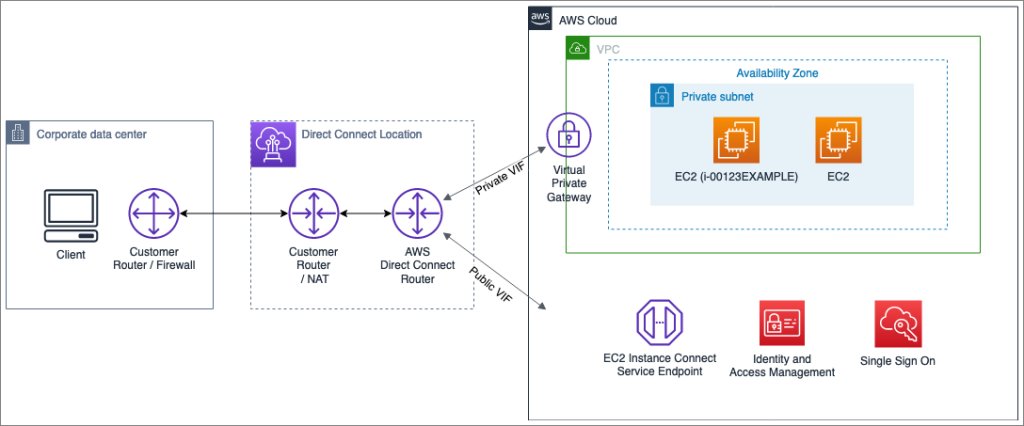
You’ve created a standard network topology for using EC2 Instance Connect as depicted in diagram. Your on-premises corporate data centre connects to the AWS Cloud via Direct Connect. it establishes a dedicated network connection between your on-premises network and an AWS Direct Connect Partner.
- 1. Network Setup:
- Your on-premises network connects to AWS via Direct Connect.
- You have a private VPC with no internet gateway, connected to your on-premises network.
- EC2 instances in this VPC have private IPs and are protected by security groups allowing SSH from your on-premises network.
- 2. IAM Policy:
- Create an IAM role that users can assume after logging in via AWS SSO.
- The role permits access to specific instances and restricts key-sending operations to your corporate network’s IP range.
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Action”: [
“ec2-instance-connect:SendSSHPublicKey”
],
“Resource”: [
“arn:aws:ec2:$REGION:$ACCOUNTID:instance/i-00123EXAMPLE”
],
“Condition”: {
“IpAddress”: {
“aws:SourceIp”: [
“198.51.100.0/24”
]
},
“StringEquals”: {
“ec2:osuser”: “ec2-user”
}
}
}
]
}
Connect to the EC2 instances using EC2 Instance Connect
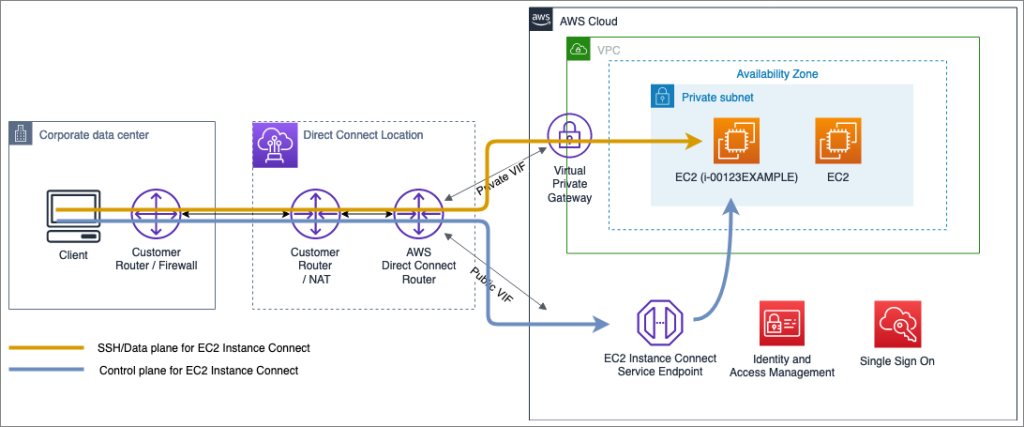
Let’s say Teja needs to connect to an instance using EC2 Instance Connect CLI. Here’s what happens:
- Generate SSH Key: A one-time SSH key is created on her machine.
- Send Public Key: The public key is sent to the EC2 Instance Connect service, which delivers it to the instance’s IMDS.
- Connect via SSH: Martha connects to the instance’s private IP using the private key within 60 seconds.
Conclusion
EC2 Instance Connect makes SSH access management easier and more secure by using temporary keys and IAM policies.
This method works for instances in both private and public subnets. By defining a network setup and using IAM policies, you can control where SSH sessions come from.
- By admin





